by Brendan Cullen
TikTok is one of today’s most popular social media platforms. With a global user base of nearly 1.6 billion, the relatively new platform has cemented itself as a leading mobile application amongst well-established media giants (Iqbal, 2023). Without any investigation, it is evident that TikTok has optimized how users engage with content. Other prominent social media platforms have tried to replicate TikTok’s successful design—YouTube’s ‘Shorts’, Instagram’s ‘Reels’, Netflix’s ‘Fast Laughs’, and Snapchat’s updates to how users view ‘Stories’ are all examples of this mimicry. TikTok has proven itself to be a leading provider of short video-based content and was the most downloaded mobile app worldwide in 2022 (Apptopia, 2023). TikTok’s popularity is highlighted by its prevalence in the United States. As of March of 2023, there were over 150 million active users in the United States, nearly 50% of the country’s population (TikTok Newsroom, 2023). The platform’s growth and success, however, has not gone untouched by controversy.
Many questions have been raised about TikTok’s extensive collection of user data and its parent company, Chinese media giant ByteDance Ltd. The platform’s integration with American citizens has led U.S. politicians and cyber professionals to question the motive behind the company’s privacy policy and its effects on the nation. Similar concerns have been raised by several European countries, India, and Australia. This thesis seeks to evaluate the validity of recent concerns regarding TikTok’s threat to U.S. National Security. The case study will begin by examining the platform’s history, design, and privacy policy. This introduction highlights the ways in which TikTok is unique from other platforms in today’s social media ecosystem and why the differences are relevant to national security concerns. Lastly, this section will detail the platform’s ties to the People’s Republic of China.
TikTok’s History and China’s Douyin
TikTok is the international version of the app “Douyin”, owned by the Chinese media conglomerate ByteDance Ltd. TikTok’s predecessor, Musical.ly, which focused on basic lip-syncing/dancing videos, was created by a Chinese tech company and specifically targeted at the U.S. market in 2014. After the platform’s success, it was bought out, re-designed, and re-marketed by ByteDance in 2017 as TikTok, as a means for ByteDance to enter the U.S. market (CRS, 2023b). This strategic move allowed ByteDance to combine the success Musical.ly had with young people in the West with the AI-driven capabilities of Douyin (Kaye et al., 2020). Douyin and TikTok appear very similar structurally and even showcase the same logo. On both platforms, users view content provided by a recommendation algorithm by swiping from video-to-video.
At a glance, the two platforms are nearly identical, but there are some very interesting differences in the user-experience. Douyin includes a second ‘Trending’ tab on its toolbar entitled “positive energy”, which is an “ideological buzzword in China that is emblematic of Chinese patriotism” (Kaye et al., p. 237). This umbrella term, also termed “playful patriotism”, signifies content that is in accordance with the values of the Chinese Communist Party (Kaye et al., p. 238). Although this feature doesn’t exist on TikTok, it is an example of how the PRC can exert influence on social media.
Through Douyin, the PRC can promote the State and filter out content that is not favorable. While TikTok has its own objectives for content moderation, the threshold for content that does not abide by Douyin’s standards is much wider. Categories for reporting on Douyin include pornography, political sensitivity, rumors/swindling, and insulting (Kaye et al., 2020). Efforts to control what Douyin users’ see and interact with are consistent with China’s internal governance of their information environment. Coined “The Great Firewall”, China employs an internally locked-down internet service. The Golden Shield Project in 2000 created a data-driven surveillance network that monitors the online activity of Chinese citizens by filtering content and enforcing censorship (Lee, 2018).
The next section will examine the PRC’s use of cyber in greater depth. But, even in this locked-down environment, the PRC has taken action to curtail the usage of Douyin in China, especially for young users. For Douyin accounts using “youth mode”, which is regulated through real-name authentication, children under the age of 14 are limited to just 40 minutes per day on the platform. There is a hard shutdown of the platform between the hours of 10 p.m. and 6 a.m. for these young users. Additionally, young Douyin users are recommended more videos that endorse science experiments, historical content, state museums, and patriotism (Wayt, 2021). ByteDance even injected a mandatory 5-second lag after some videos, in an effort to prevent addiction amongst Chinese youth (Humphries, 2021).
Some important conclusions can be drawn from these policies. ByteDance, which is innately and unquestionably tied to the CCP, designed TikTok to be targeted at the U.S. market. After doing so, significant regulations were implemented that influence how children use Douyin, China’s internal, restricted version of TikTok. This timeline indicates that the PRC sees a serious problem with how the platform affects their nation’s youth. They do not want their young citizens to engage in fad trends and strive to be culture “influencers.” Rather, they want to reduce entertainment-media addiction, endorse nationalistic ideology, and promote STEM related careers. Despite this stark reality, the United States leaves its youth unguarded on TikTok. Awareness of TikTok’s history is critical to understanding the potential implications of its use in the United States.

TikTok’s Design and Privacy Policy
TikTok’s persuasive design and cutting-edge algorithmic recommendation system have revolutionized how social media platforms appeal to users. The platform’s architecture establishes an intimate relationship with the user. Following the demands of surveillance capitalism, the ‘For You Page’ on TikTok provides users with strategically curated content and advertisements based on various sources of data. White space (negative space between features) is eliminated entirely on this feed by embedding actionable icons (like, comment, share, etc.) directly onto videos. Eliminating white space and embedding interactive features persuades users to remain immersed in the infinite feed of personalized content.
TikTok’s popularity, especially with younger generations, indicates the success of the platform’s user-interface (UI) and user-experience (UX). According to a 2022 survey of American teenagers ages 13 to 17 by the Pew Research Center, 67% have ever used TikTok and 16% claim they use it constantly (Vogels et al., 2022). Another study, conducted by non-profit Common Sense Media and University of Michigan C.S. Mott Children’s Hospital, determined that the median time spent on TikTok by children per day was 1 hour and 52 minutes (Radesky et al., 2023). The research sample consisted of 203 children aged 11-to 17-year-olds on Android phones. The study also noted that children were more likely to spend several hours (sometimes upwards of 7 hours) on the platform, while 3 hours was the longest amount of time spent on Instagram or Snapchat (Radesky et al., p.7). The following excerpt, synthesized from two quotes provided by 11th graders in the report, perfectly captures youth sentiments surrounding TikTok:
Youth advisors explained to us that TikTok provides an experience that other social or video-sharing platforms don’t. TikTok was described as “easy” because videos simply start to play— the user doesn’t have to make any decisions, so there’s no friction. Adolescents we talked to said that the TikTok algorithm “knows” them so well, they can expect that they will likely find something fun to watch. If the user isn’t interested in the video that starts to play, the app quickly adapts to something more engaging or that fits their mood or desires (Radesky et al., p. 7)

Social platforms are deliberately constructed to maximize engagement. The results of this study indicate that children are highly receptive to TikTok, largely due to the accuracy of recommendations. TikTok’s eerie ability to predict desirable content stems from its extensive collection of user data.
Although the social media ecosystem is built on data collection, TikTok’s privacy policy is cause for immediate concern. Given the platform’s ties to China, it is extremely relevant to review the company’s policy and connections to the PRC. Although the policy is too long to review in its entirety within this paper, this section will review some of its key elements.
TikTok, of course, collects basic account information (name, age, language, email, phone number, profile image, etc.) and user-generated content (TikTok, 2023a). But according to technical analysis of TikTok’s source code conducted by cyber security company Internet 2.0 in July of 2022, the “Permissions and device information collection are overly intrusive and not necessary for the application to function” (Perkins, 2022, p. 1). TikTok automatically collects device identifiers such as IP address, mobile carrier, device system, network type, screen resolution, operation system, app and file names and types, battery state, audio settings, and keystroke patterns or rhythms.
The platform also claims it may associate users with information collected from devices they do not use TikTok on (TikTok, 2023a). Some of this information is typically collected by social platforms. However, the collection of keystroke patterns could enable the platform to know specific actions users take outside of the platform, including what users type. Collection of keystroke patterns, which is typically a function of malware tools, might reveal users’ login credentials, payment information, message content, and more (Mozur et al., 2022). Internet 2.0 claims that TikTok’s data collection allows for device mapping, meaning that theoretically the platform could deduce the layout of your phone (Perkins, 2022).
From user-generated images and videos, TikTok can collect “face and body features and attributes”, “the existence and location within an image of face and body features and attributes”, and biometric identifiers such as faceprints and voiceprints (TikTok, 2023a). TikTok can scan and analyze messages on the app for content and even view the text, images, and videos found in the device’s clipboard. Additionally, the platform can access users’ phone and social network contacts. Through third-party associations and cookies, TikTok can gain access to users’ activity on other sites and across devices. Conveniently, the platform is not responsible for the privacy practices of its providers and affiliates (TikTok, 2023a).

A section of the policy titled “How We Use Your Information” details how user data is applied to platform improvement, troubleshooting, targeted ads, algorithm training, and more. This section closes by reserving the right to combine any information they collect or receive and use it for any purposes they disclose at the time of consent (TikTok, 2023a). TikTok has a separate privacy policy directed to children under the age of 13 that use “Kid’s Mode”. While this version of the app collects limited data, the platform still reserves the right to share information with their corporate group as needed (TikTok, 2023b).
The platform’s privacy policy also explains that entities in TikTok’s corporate group have “limited remote access” to the information the platform collects (TikTok, 2023a). To the uninformed reader, this is likely a benign statement. TikTok’s corporate group obviously would include its Beijing-based parent company, ByteDance Ltd. The diagram in Figure 1 below, taken from ByteDance’s website, shows how TikTok fits into ByteDance’s corporate structure.
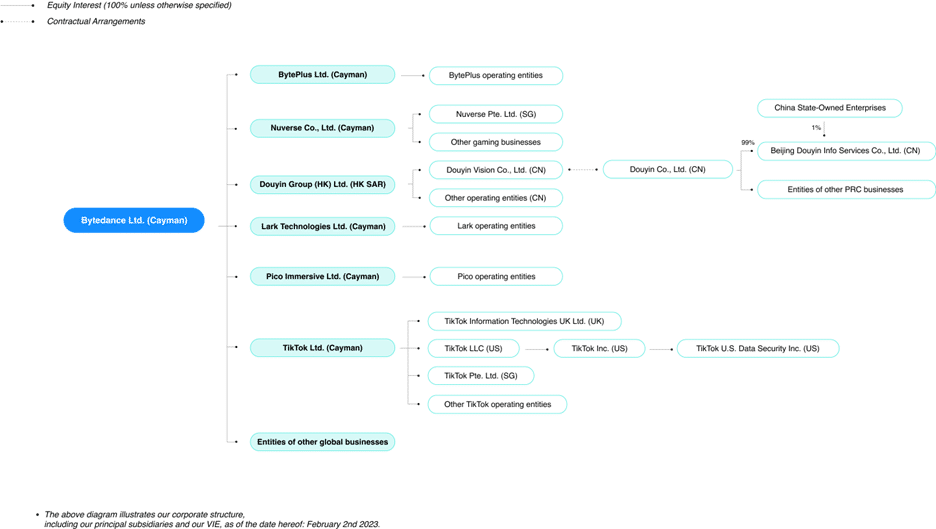
Figure 1: ByteDance Ltd.’s Corporate Structure
Based on this diagram, ambiguous “China State-Owned Enterprises” have a 1% stake in Beijing Douyin Info Services Co., Ltd., which is contractually connected to TikTok’s parent-company ByteDance. TikTok’s CEO, Shou Zi Chew, claims that this 1% acquisition was necessary to obtain a news license in China for several China-based applications such as Douyin (Chew, 2023). Douyin Co., Ltd. is also tied to “Entities of other PRC businesses.” These connections indicate that some of ByteDance’s subsidiaries are likely subject to PRC legislation. Despite ByteDance’s corporate structure, TikTok asserts that all data is stored in the U.S. and Singapore and the company would not share data with the Chinese government if asked. However, TikTok’s efforts to portray independence from China disregard ByteDance’s ability to access data. ByteDance and other PRC-based companies are subject to the PRC’s cyber security and intelligence laws, which presents a threat to the United States.
Today, TikTok maintains offices in major U.S. cities such as Los Angeles and New York (CRS, 2023b). According to the Washington Post, some high-level executives have transferred from ByteDance to TikTok in 2023, some of which even relocated to the United States from ByteDance’s Beijing headquarters (Wells, 2023). In response to pressure by the U.S., TikTok has tried to show its separation from the PRC by contracting with Oracle, an American software giant, in a partnership referred to as “Project Texas” (Chew, 2023). In a letter to nine U.S. Republican Senators, TikTok’s CEO Shou Zi Chew claimed that the company has not and would not provide data to the CCP. In the same letter, however, he concedes that China-based employees could access user data in some cases. ByteDance engineers around the world work on TikTok’s algorithm, and TikTok employees use software provided by ByteDance (Chew, 2023). Despite attempts to show allegiance to the U.S. interests and privacy, ByteDance’s ties to the CCP should not be overlooked.

Conclusions
TikTok’s connection to Beijing via ByteDance Ltd. has been a primary cause of concern for the United States Government. Amidst continued and escalating tension between the two countries, the U.S. seeks to protect its assets and its citizens from PRC influence. Given TikTok’s widespread integration with U.S. citizens, particularly children, the United States should be wary to accept the platform’s operations in the country. TikTok’s extensive collection of user data and persuasive design make it a particularly effective vehicle for information operations, propaganda, and cyber operations.
Additionally, a Beijing-based media company like ByteDance is innately tied to the Chinese government due to the country’s employment of digital authoritarianism. The PRC uses technology as a force multiplier to control its own citizens and exercise power abroad. For these reasons, TikTok should be addressed with caution and investigated for its threat potential.
______________________________
Brendan Cullen is a senior Cyber Policy & Ethics and Criminology & Criminal Justice double major at the University of South Carolina Honors College. Brendan is a prospective Master of Science in Global Security, Conflict, and Cybercrime (MSGSCC) student at NYU’s School of Professional Studies. Brendan has experience interning as a Summer Security Analyst for Related Companies, and as an Undergraduate Research Assistant for the University of South Carolina’s Social Media Insights Lab.
He has also served as a Part-Time Consultant for Moth+Flame VR, an immersive training technology developer, for almost two years. Brendan’s undergraduate Honors Thesis, “Assessing the Threat of Social Media to National Security: Information Operations in the 21st Century,” investigates social media’s capacity for malign influence and espionage. Specifically, his research assesses the threat that TikTok poses to U.S. National Security.
As the Voice of the Veteran Community, The Havok Journal seeks to publish a variety of perspectives on a number of sensitive subjects. Unless specifically noted otherwise, nothing we publish is an official point of view of The Havok Journal or any part of the U.S. government.
References
Apptopia. (2023). Leading mobile apps worldwide in 2022, by downloads (in millions). Statista. https://www.statista.com/statistics/1285960/top-downloaded-mobile-apps-worldwide/.
ByteDance. (n.d.). Corporate Structure. https://www.bytedance.com/en/.
ByteDance. (n.d.). Locations. https://jobs.bytedance.com/en/footprint.
Cheng, D. (2003). Winning without fighting: the Chinese psychological warfare challenge. The Heritage Foundation. https://www.heritage.org/global-politics/report/winning-without-fighting-the-chinese-psychological-warfare-challenge.
Chew, S. (2022). Letter to Senators Blackburn, Wicker, Thune, Blunt, Cruz, Moran, Capito, Lummis, and Daines. https://www.blackburn.senate.gov/services/files/A5027CD8-73DE-4571-95B0-AA7064F707C1.
Collins, B. (2022). TikTok ‘Invisible Body Challenge’ hijacked to spread malware. Forbes. https://www.forbes.com/sites/barrycollins/2022/11/29/tiktok-invisible-body-challenge-hijacked-to-spread-malware/?sh=9953ab078ad1.
Congressional Research Service. (2023b). TikTok: Technology Overview and Issues. https://crsreports.congress.gov/product/pdf/R/R46543.
Congressional Research Service. (2023c). China’s “One Belt, One Road” Initiative: Economic Issues. https://crsreports.congress.gov/product/pdf/IF/IF11735.
Evanina, W. (2019). “NCSC Director Warns of Nation-State Cyber Threats to Law Firms in June 4 Remarks at ILTA LegalSEC Summit 2019”. The Office of the Director of National Intelligence. https://www.dni.gov/index.php/ncsc-newsroom/3346-ncsc-director-warns- of-nation-state-cyber-threats-to-law-firms-in-june-4-remarks-at-ilta-legalsec-summit-2019.
Exec. Order No. 13959. (2020). 85 FR 73185. https://www.federalregister.gov/d/2020-25459.
Gering, T. (2023). “Full throttle in neutral: China’s new security architecture for the Middle East”. Atlantic Council. https://www.atlanticcouncil.org/in-depth-research-reports/issue-brief/full-throttle-in-neutral-chinas-new-security-architecture-for-the-middle-east/.
Humphries, M. (2021). China’s TikTok adds mandatory 5-second pause between videos. PcMag. https://www.pcmag.com/news/chinas-tiktok-adds-mandatory-5-second-pause-between- videos#:~:text=As%20the%20South%20China%20Morning,too%20long%20continuousl y%20watching%20videos.
Iqbal, M. (2023). TikTok revenue and usage statistics. BusinessOfApps. https://www.businessofapps.com/data/tik-tok-statistics/.
Kaye, D. B. V., Chen, X., & Zeng, J. (2021). The co-evolution of two Chinese mobile short video apps: Parallel platformization of Douyin and TikTok. Mobile Media & Communication, 9(2), 229-253.
Laskai, L., & Segal, A. (2018). A new old threat: Countering the return of Chinese industrial cyber espionage. Council on Foreign Relations. http://www.jstor.org/stable/resrep29903.
Lee, J. A. (2018). Great firewall. The Chinese University of Hong Kong Faculty of Law. Research Paper No. 2018-10.
Lorenz, T. (2023). Why TikTok videos on the Israel-Hamas war have drawn billions of views.The Washington Post. https://www.washingtonpost.com/technology/2023/10/10/tiktok-hamas-israel-war-videos/.
Maheshwari, S. (2023). TikTok’s C.E.O. uses personal touch to address antisemitism concerns. The New York Times. https://www.nytimes.com/2023/12/01/business/shou-chew-tiktok- antisemitism.html.
Maheshwari, S. & Holpuch, A. (2023). Why countries are trying to ban TikTok. The New York Times. https://www.nytimes.com/article/tiktok-ban.html.
Matsa, K. (2023). More Americans are getting news on TikTok, bucking the trend seen on most other social media sites. Pew Research Center. https://www.pewresearch.org/short- reads/2023/11/15/more-americans-are-getting-news-on-tiktok-bucking-the-trend-seen-on-most-other-social-media-sites/.
Moench, M. & Shah, S. (2023). Why Osama bin Laden’s ‘Letter to America’ went viral on TikTok. Time. https://time.com/6336280/osama-bin-laden-letter-to-america-tiktok/.
Morris, S. & Kinder, T. (2022). HSBC installs Communist party committee in Chinese investment bank. Financial Times. https://www.ft.com/content/eac99fd9-0c30-4141- 821a-45348f61c113.
Mozur, P., Mac, R., & Che, C. (2022). TikTok browser can track users’ keystrokes, according to new research. The New York Times. https://www.nytimes.com/2022/08/19/technology/tiktok-browser-tracking.html.
Perkins, T. (2022). TikTok Analysis. Internet 2.0. https://tinyurl.com/39x7m5zt.
Radesky, J., et al. (2023). Constant Companion: A Week in the Life of a Young Person’s Smartphone Use. Common Sense & C.S. Mott Children’s Hospital. https://www.commonsensemedia.org/sites/default/files/research/report/2023-cs-smartphone-research-report_final-for-web.pdf.
Smith, H. (2023). Chinese spies are targeting access, not race. Foreign Policy. https://foreignpolicy.com/2023/09/22/china-spying-race-intelligence-targeting/.
Stockton, J. (2021). Defeating Coercive Information Operations in Future Crises. The Johns Hopkins University Applied Physics Laboratory LLC. https://www.jhuapl.edu/sites/ default/files/2022-12/DefeatingCoerciveIOs.pdf.
The White House. (2021). FACT SHEET: Executive Order Addressing the Threat from Securities Investments that Finance Certain Companies of the People’s Republic of China. https://shorturl.at/vIMNR.
TikTok. (2023a). Privacy Policy. https://www.tiktok.com/legal/page/us/privacy-policy/en.
TikTok. (2023b). Children’s Privacy Policy. https://www.tiktok.com/legal/page/global/childrens- privacy-policy/en.
TikTok Newsroom. (2023). Celebrating our thriving community of 150 million Americans. https://newsroom.tiktok.com/en-us/150-m-us-users.
U.S. Department of Defense. (2023a). 2023 DOD Cyber Strategy Summary.
U.S. Department of Defense. (2023b). Military and Security Developments Involving the People’s Republic of China. https://media.defense.gov/2023/Oct/19/2003323409/-1/-1/1/2023-military-and-security-developments-involving-the-peoples-republic-of-china.pdf.
Vogels, E., Gelles-Watnick, R., & Massarat, N. (2022). Teens, Social Media and Technology 2022. Pew Research Center. https://www.pewresearch.org/internet/2022/08/10/teens-social-media-and-technology-2022/.
Wayt, T. (2021). Douyin, Chinese version of TikTok, adds time limit for kids under 14 and bans nighttime use. New York Post. https://nypost.com/2021/09/20/chinese-version-of-tiktok-adds-time-limit-for-kids-bans-nighttime-use/.
Wells, G. (2023). TikTok employees say executive moves to U.S. show China parent’s influence. The Wall Street Journal. https://www.wsj.com/tech/tiktok-employees-say-executive-moves-to-u-s-show-china-parents-influence-ef5ff21f.
Wenling, D. & Jiali, L. (2023). Cognitive confrontation on the social media battlefield. People’s Liberation Army Daily.
Wortzel, L. M. (2014). The Chinese People’s Liberation Army and Information Warfare. Strategic Studies Institute, US Army War College. http://www.jstor.org/stable/resrep11757.
WSJ Staff. (2021). Inside TikTok’s algorithm: A WSJ video investigation. The Wall Street Journal. https://www.wsj.com/articles/tiktok-algorithm-video-investigation- 11626877477.
X Blog. (2020). Disclosing networks of state-linked information operations we’ve removed. X. https://blog.twitter.com/en_us/topics/company/2020/information-operations-june-2020.
Buy Me A Coffee
The Havok Journal seeks to serve as a voice of the Veteran and First Responder communities through a focus on current affairs and articles of interest to the public in general, and the veteran community in particular. We strive to offer timely, current, and informative content, with the occasional piece focused on entertainment. We are continually expanding and striving to improve the readers’ experience.
© 2024 The Havok Journal
The Havok Journal welcomes re-posting of our original content as long as it is done in compliance with our Terms of Use.










Leave a Reply